How to Configure and Use Hardware Yubikey with Mac OS SSH
Due to recent updates to OpenSSH there is now a much simpler and easier way to use hardware tokens for SSH access.
Start by inserting your Yubikey into your Mac.
Create a new key ecdsa-sk which will reside on your machine but require your hardware token:
ssh-keygen -t ecdsa-sk -f ~/.ssh/id_ecdsa_sk -C “user@site.co”It’ll ask you to enter a password to protect your key, then if touch compatible you’ll need to press the light when asked.
Copy the contents of ~/.ssh/id_ecdsa_sk.pub to the .ssh/authorized_keys file on your remote server and then you’re ready to test the connection works, login using your new identity:
ssh -i ~/.ssh/id_ecdsa_sk user@server.comYou’ll then be protected for your key password, then prompted to authorise the connection request by touching your hardware key:
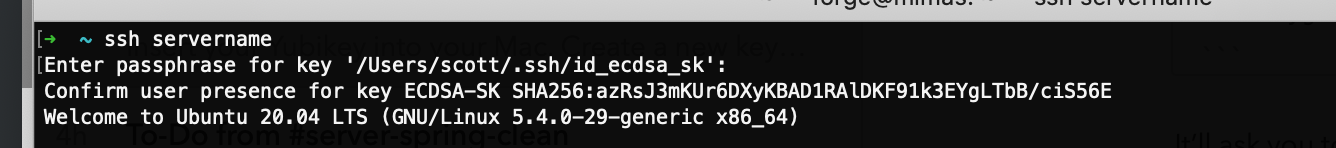
It makes it easier to store the identity file in your .ssh/config file so you don’t have to type it out each time, use a configuration like this:
Host servername
User ssh-username
Hostname servername.server.tld
Port 22
IdentityFile ~/.ssh/id_ecdsa_skThis now means that you can just type ssh servername and it’ll automatically use the right user, hostname, port and key.
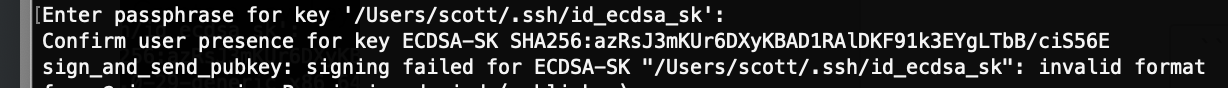
…and without the hardware key?
If you don’t have your hardware key plugged in to you machine when you try to connect, then you’ll get this error: